 ×
×
 ☰
☰
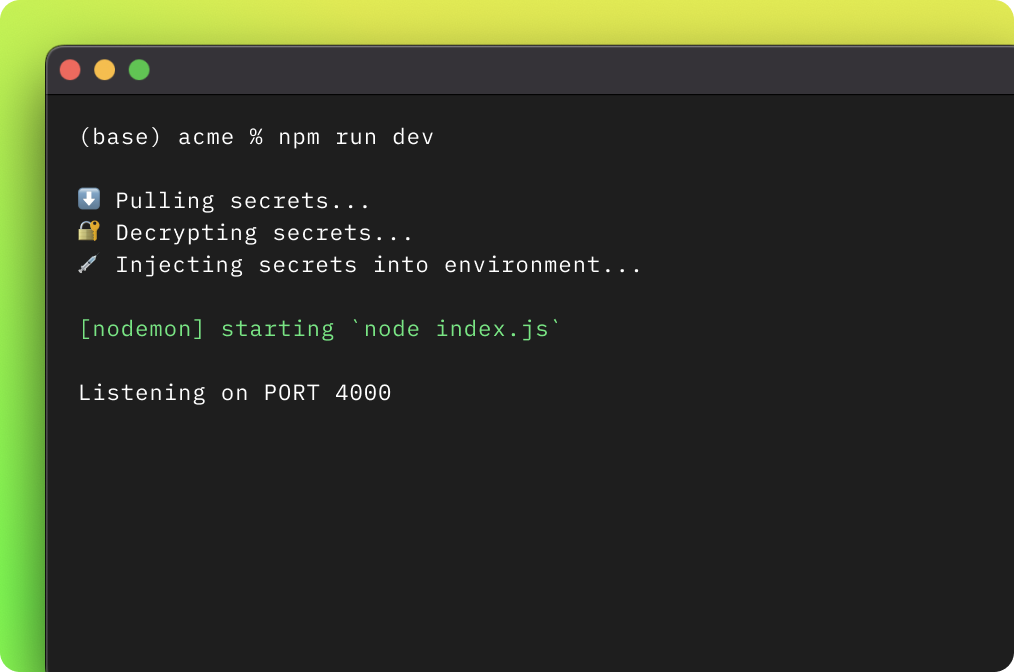
Injecting environment variables into your environment
Like many full stack developers, I began my foray into programming through online courses on Udemy where I learned to build and deploy applications on Heroku. Fast forward 5 years later, my tech-stack evolved to include tools like Next.js and Apollo GraphQL but many principles stayed the same — one such principle was how I handled environment variables with .env files in Node.js.
For context, if you’re unfamiliar with .env files, check out my primer here. They’re a simple but flawed way to store environment variables because of how easily it is to mishandle them. Here are a few common issues that I’ve seen arise in dev teams:
It’s clear that a better approach is needed to prevent environment variables from getting accidentally leaked, stop developers from having to send variables over email to keep files in sync, and save debugging hours on missing keys and configs.
It turns out that better solutions do exist in the form of secret managers that allow you to securely store and pull back environment variables into your local processes. That said, many of them like Vault can be cumbersome and frankly overkill to set up depending on the size of your projects.
Seeing this gap, we’ve made an open-source solution called Infisical. It’s an end-to-end encrypted platform that dev teams use to upload their environment variables, view and manage them, and enable their devs to easily pull and inject back values into their local processes. It comes built in with secret versioning, snapshots, and audit logs.

Source: Medium